Extended Abstract: Oscur0: One-Shot Circumvention without Registration
Authors: Mingye Chen (University of Michigan), Jack Wampler (University of Colorado Boulder), Abdulrahman Alaraj (University of Colorado Boulder), Gaukas Wang (University of Colorado Boulder), Eric Wustrow (University of Colorado Boulder)
Year: 2024
Issue: 1
Pages: 32–34
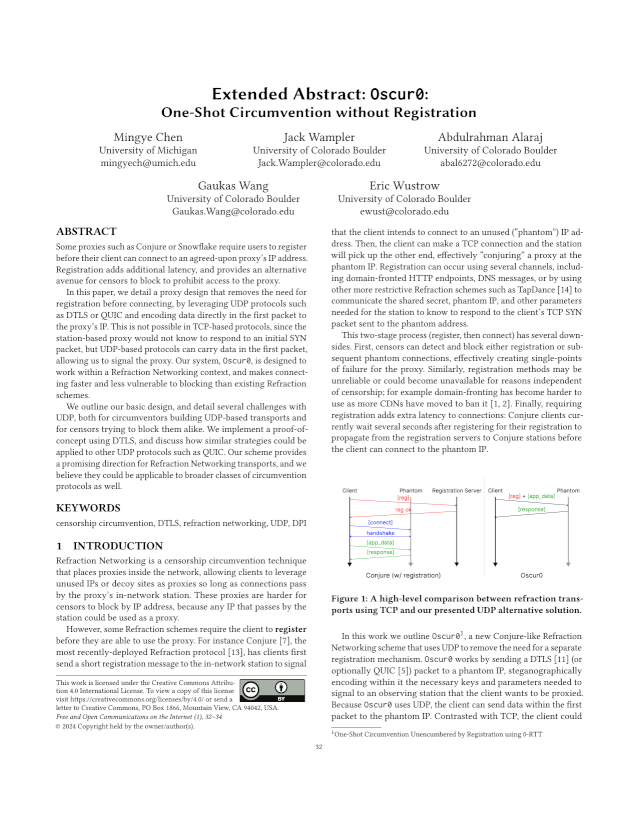
Abstract: Some proxies such as Conjure or Snowflake require users to register before their client can connect to an agreed-upon proxy’s IP address. Registration adds additional latency, and provides an alternative avenue for censors to block to prohibit access to the proxy. In this paper, we detail a proxy design that removes the need for registration before connecting, by leveraging UDP protocols such as DTLS or QUIC and encoding data directly in the first packet to the proxy’s IP. This is not possible in TCP-based protocols, since the station-based proxy would not know to respond to an initial SYN packet, but UDP-based protocols can carry data in the first packet, allowing us to signal the proxy. Our system, Oscur0, is designed to work within a Refraction Networking context, and makes connecting faster and less vulnerable to blocking than existing Refraction schemes. We outline our basic design, and detail several challenges with UDP, both for circumventors building UDP-based transports and for censors trying to block them alike. We implement a proof-of-concept using DTLS, and discuss how similar strategies could be applied to other UDP protocols such as QUIC. Our scheme provides a promising direction for Refraction Networking transports, and we believe they could be applicable to broader classes of circumvention protocols as well.
Copyright in FOCI articles are held by their authors. This article is published under a Creative Commons Attribution 4.0 license.